CYBERSECURITY
The Threat to Small and Mid Sized Businesses Is Real
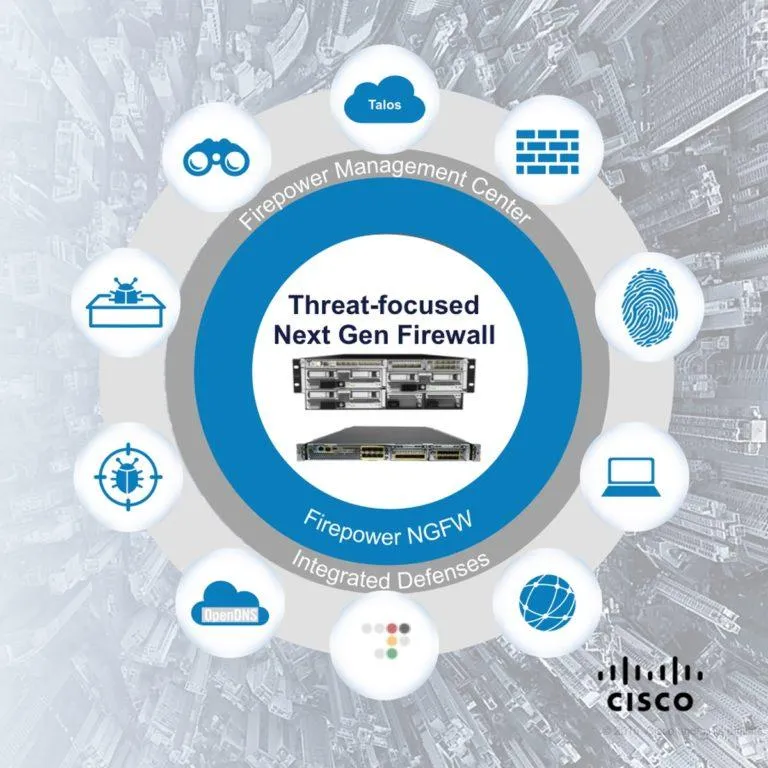
Next Generation Firewall
Still calling it a router? While a firewall has routing capability, it can do much more than that. A router directs traffic while a firewall inspects that traffic to make sure that it is safe for your network. A Next Generation Firewall (NGFW) takes that inspection to a whole new level with deep packet inspection that looks at the behavior and intended application of each packet. NGFWs can use external data sources to identify threats and even sandbox data to validate it before allowing the traffic to enter your network. A NGFW is the foundational element to your cybersecurity defensive posture and the gatekeeper to your network.
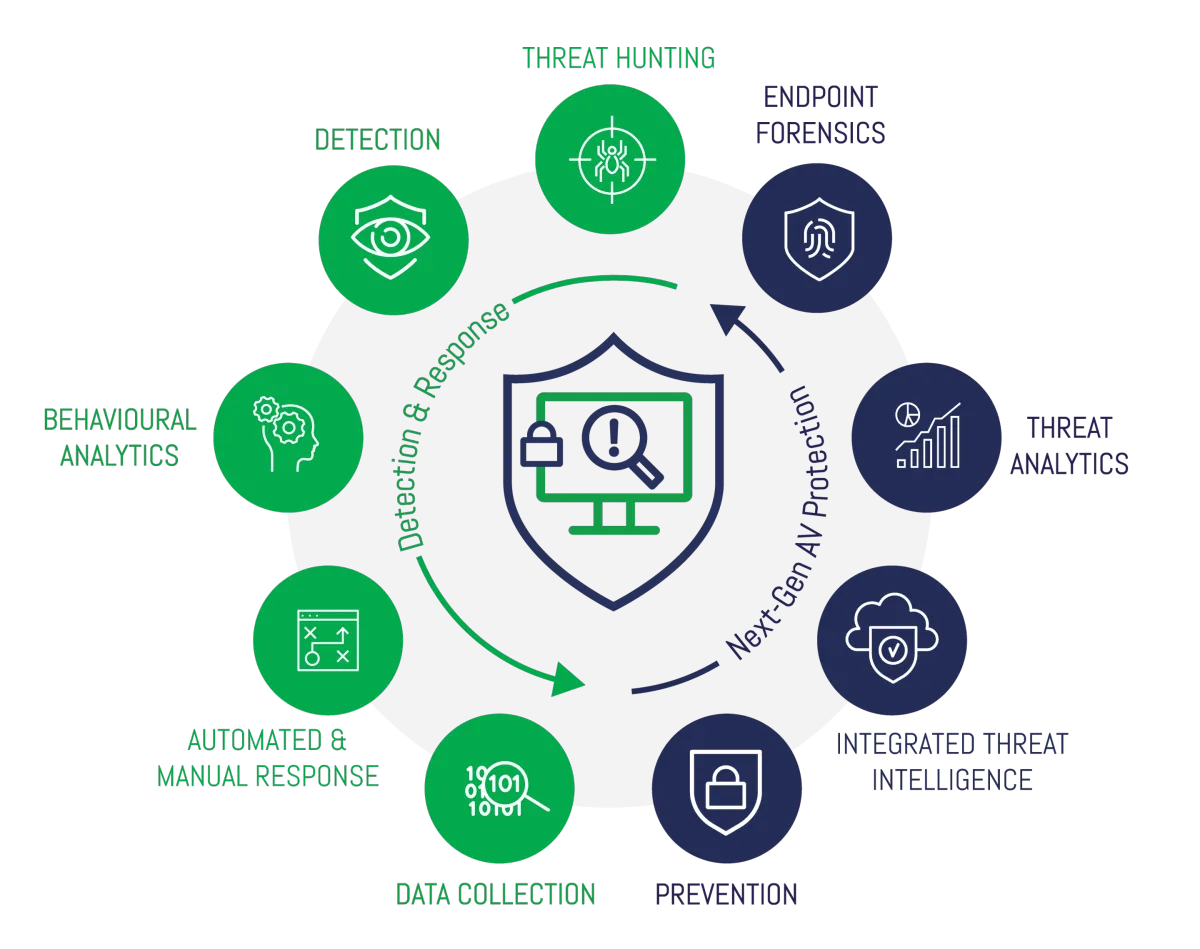
Endpoint Detection & Response
Antivirus is no longer a viable defense on your network. Antivirus acts only on known viruses and malware. Every day hackers are developing new and more dangerous viruses and malware. These are often released and cause significant damage well before they are isolated, identified, and written into an Antivirus update. Endpoint Detection and Response (EDR) is designed to work like antivirus, but EDR also protect against unknown threats. EDR looks not only at the application data, but also the application's behavior on the endpoint to protect the user. Advanced EDR programs can also isolate infected machines from the rest of the network to keep the virus or malware from spreading to other systems.
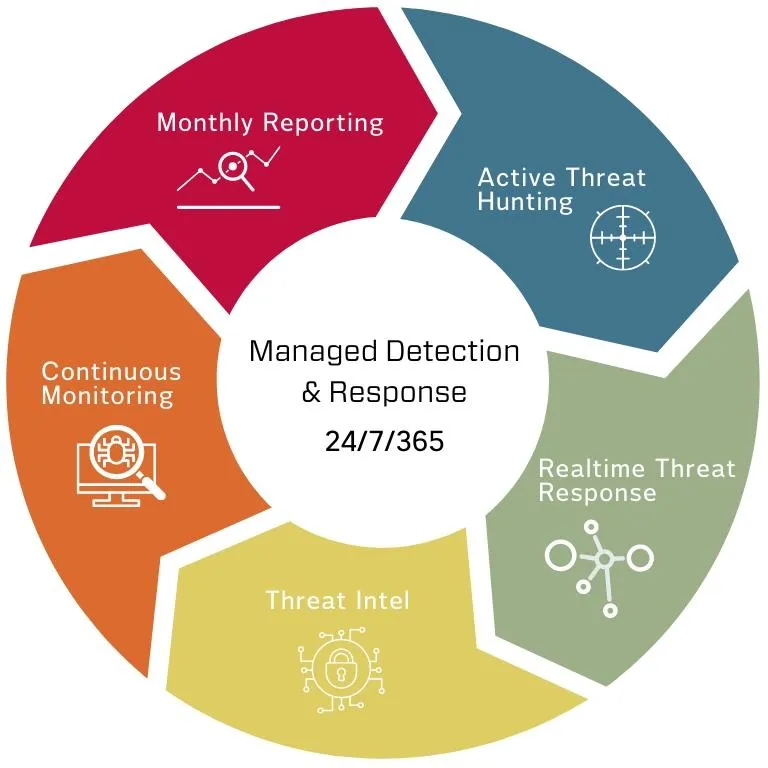
Managed Detection & Response
Managed Detection and Response is the next level of network security that works with your antivirus or EDR and offers more protection. While EDR focuses on the endpoint (PC), MDR looks across the network holistically including endpoints, cloud, IoT devices, and mobile devices and ingests data from multiple sources like logs, events, and activities to detect and respond to threats in real time. MDR also adds an element of human expertise, offering threat intelligence analysis, incident response support, and 24/7 access to a skilled security team.

Zero Trust
The highest level of network security, Zero Trust Network Architecture (ZTNA) operates under the premise that all users and devices on the network need to be verified before they can be trusted. Traditional network architecture trusts all users and devices inside the network. ZTNA trusts nothing and no one and requires verification for any user or device to connect, regardless of its location. ZTNA can prevent users and devices from accessing specific applications, data, storage, or other devices based on permissions.
Email Defense
Just like the title, email defense protects your organization from threats traversing email messages. This goes beyond just advanced SPAM blocking and email filtering and also includes inspection of other aspects of email messages to prevent VIP impersonations, malicious links and attachments, and even images and QR codes that could be harmful to your users or organization. Most hackers rely on the human element to gain access to your network and email is the frontline for most businesses when it comes to engaging with your employees.

Security Awareness Training
Verizon's most recent data breach report statistics show that 74% of all breaches include the human element, with people being involved either via error, privilege misuse, use of stolen credentials, or social engineering. Firewall and EDR won't help you when your employees are the ones opening the door. Educating your employees on current social engineering tactics and what to look out for regarding malicious actors is key in sharpening your cyber defense.
